Pozyx
Most popular related searches
Turn Location Data Into Action
Your location data is more than just dots on a map—use it to drive automation and efficiency:
Geofencing
Create virtual zones to trigger automatic actions when assets enter or leave designated areas.
No-code Rule Engine
Define custom rules to automate actions based on real-time location events and conditions. Learn more.
Alerts & Notifications
Get instant updates on critical movements and status changes, so you’re always in control.
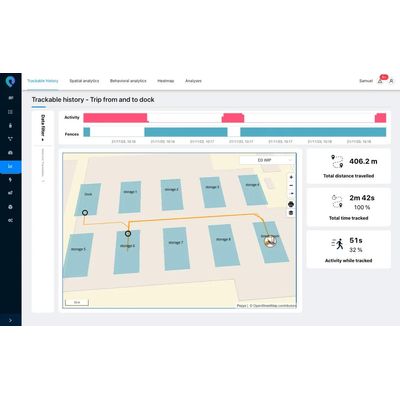
The Most Powerful Location Analytics
Go beyond real-time tracking—analyze movement patterns, optimize operations, and make data-driven decisions
- Replay Function – Step back in time to visualize past asset movements and events.
- Heatmaps – Identify activity hotspots and optimize resource allocation.
- Spaghetti Charts – Analyze movement flows to uncover inefficiencies and bottlenecks.
- Reports – Generate detailed insights to track trends and improve decision-making with over 15 unique downloadable reports.
- Dashboards – easily connect to your favourite BI tool.
Transform raw location data into actionable intelligence to drive efficiency and performance.
Seamless Access to Your Location Data
Unlock the full potential of your location data with easy and flexible integration options.
Data, your way
- Middleware Integrations – Connect effortlessly with ERP, WMS, and MES systems to automate workflows and enhance operations.
- MQTT – Lightweight, real-time data streaming for fast and efficient communication.
- Omlox Hub API – A standardized API for seamless access to real-time location data and events.
Enterprise-Grade Security You Can TrustSecurity is at the core of our platform, ensuring your data remains protected at all times. Our solution is designed with robust security features to meet the highest industry standards:
- Flexible Deployment – Deploy on-premise or in an isolated cloud for full control over your environment.
- Single Sign-On (SSO) – Streamline authentication with seamless enterprise integration.
- Multi-Factor Authentication (MFA) – Add an extra layer of protection to user logins.
- Role-Based Access Control (RBAC) – Ensure users only access what they need, reducing security risks.
- Automated Backups – Maintain data integrity and business continuity with redundant backups.
- ISO 27001:2022 Certified – Built to comply with the highest international security standards.